The most comprehensive deception solution in the industry


Duration : Less than 5 minutes
Baits, Lures, breadcrumbs, honeytokens, Decoys
(APIs & Micro Services), Enterprise Scale, IoT-Scale Architecture

Acalvio is the first to offer a unified platform for public, private, and hybrid cloud deception. ShadowPlex Cloud represents a new benchmark in deception technology ease of deployment, detection efficacy, scalability, user experience and API support.
—Jack Poller, Senior Analyst at Enterprise Strategy Group
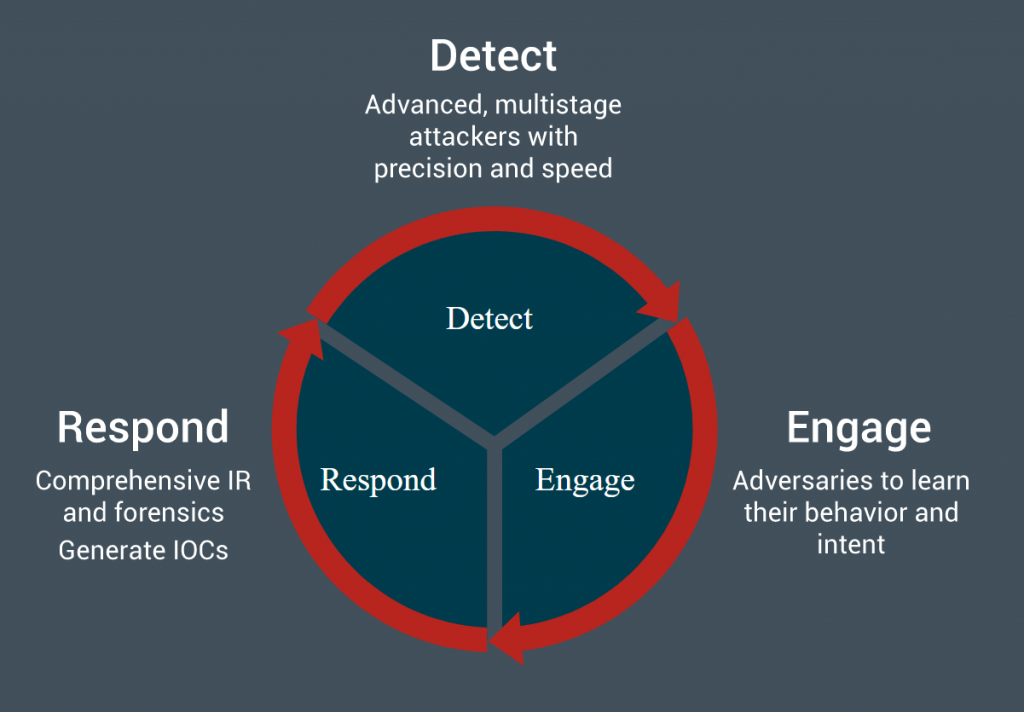
Enterprise deception solutions should scale up cost-effectively to deploy thousands of decoys, while also providing the ability to engage and respond to the attack.
Solutions that provide only one or the other are based on the first iteration of the deception technologies
Staleness is the enemy of deception. As the network and threat environments evolve, deception must adapt.
Solutions with static deceptions are easy to fingerprint and are of little value.
Effective deception needs various kinds of decoys, baits, lures and breadcrumbs
Solutions that are decoy-only (or even worse honeypot-only) or breadcrumbs-only are partial, incomplete and marginally effective solutions
An enterprise-scale deception solution needs to lay out a multitude of deceptions and manage them dynamically. Automation of every step is a requirement for practical deception at scale.
Solutions that require manually deploying or managing deceptions do not scale.
Deception technologies, by design, introduce vulnerable systems in the enterprise network to lure and engage attacks. A vulnerable system increases the risk of compromise as the threat actor can use this as a pivot point to launch attacks against other systems in the network.
Solutions that physically locate high-interaction decoys in the enterprise network (connected directly to an access port or a trunk port) run the risk of compromise pivoting to the enterprise servers.
Data science is an integral part of an effective deception solution. Machine intelligence is imperative for automation.
Beware of solutions that do not leverage machine intelligence. The effort involved to design, deploy, manage, monitor deceptions and correlate threat data is near untenable without the uncanny leverage of Data Science.
A deception should not look any different from the network neighborhood. This applies to all decoys, baits and breadcrumbs. Requires dynamic deception to keep up with the changes in the network.
Solutions that need manual setup for blending do not scale.
A deception solution must be driven by the vulnerabilities in the network and the current threat landscape. Integration with the SIEM and cyber threat feeds is essential for effective deception.
Solutions that do not integrate with the SIEM cannot be dynamic.
Threat engagement and analysis is an intrinsic part of a complete deception solution. A thorough understanding of the attack helps fix all vulnerabilities targeted by the attack and close all back doors to completely neutralize the attack.
Solutions that do not provide attack TTPs are equivalent to low interaction solutions
A deception solution cannot function in isolation. It needs to integrate with the security ecosystem to both provide effective deception and quick response.
Solutions that do not interact with the security ecosystem cannot respond to the attacks.
Traditional deception offerings are plagued with a conundrum – do you deploy lots of inexpensive low interaction decoys that provide breadth and coverage but no depth; OR a few high interaction decoys that provide depth and detail but are expensive. Through Fluid Deception technology, ShadowPlex delivers the best of both worlds. The result is cost-effective deceptions at scale, offering excellent Total Cost of Ownership.
ShadowPlex supports the most comprehensive palette of deceptions: lures, baits, breadcrumbs, honeytokens and decoys. This pervasive approach allows organizations to launch an effective and efficient campaign to combat advanced attackers. Acalvio’s patented innovations allow ShadowPlex Fluid Deception to project the behavior of assets that are not otherwise easily virtualized or emulated [examples include IoT devices, CAT Scanner, Dialysis Pumps, Routers, Switches, ICS controllers, etc.]
First generation Deception solutions are saddled with legacy architectures. In contrast, ShadowPlex is based on modern technology foundations such as API-driven Micro-services, Kubernetes and Cloud-native with full support for on-premises and AI-powered to reduce manual overhead
Acalvio provides Advanced Threat Defense (ATD) solutions to detect, engage and respond to malicious activity inside the perimeter. The solutions are anchored on patented innovations in Deception and Data Science. This enables a DevOps approach to ATD, enabling ease of deployment, monitoring and management. Acalvio enriches its threat intelligence by data obtained from internal and partner ecosystems, enabling customers to benefit from defense in depth, reduce false positives, and derive actionable intelligence for remediation.
Cyberton Global DMCC
#2905, BB2, MBA, JLT
Dubai
United Arab Emirates
Call : +971 4 520 8625 | +971 50 2028970
Email : info@cyberton.ae
GPS : 25°04’10.1″N 55°08’45.1″E